If you are an individual looking to elevate your cybersecurity career, check our offers from here
AI Investigate Leverage AI to Detect Targeted Attacks
Stop paying for managed detection response services, leverage our expertise & state-of-the-art AI to stop hidden threats & improve your security posture with a fraction of the cost
Trusted By Industry Leaders




Security Challenges
The Threat Landscape Is Evolving Faster Than Ever
SOC teams are overwhelmed, while cybercriminals are becoming more sophisticated.
Ransomware Surge
500%
Increase in ransomware attacks targeting SMBs in the past two years
Average ransom demand increased to $1.2M in 2023
Alert Fatigue
11,000
Average daily alerts, with only 28% investigated
SOC teams spend 25% of their time on false positives
Expertise Gap
$150K+
Annual cost per security analyst
MDR services starting at $25K/month
Growing Attack Surface
- 67% increase in spear-phishing attacks targeting SMBs
- 89% of ransomware attacks start with endpoint compromise
- Average detection time: 207 days
Resource Reality
- 76% of SMBs can't afford dedicated security teams
- 3.5M unfilled cybersecurity positions globally
- 62% increase in cybersecurity costs year-over-year
Why MalTrak
Multiply Your Security Capabilities
From Symantec's Attack Investigation Team to your security operations, we bring Fortune 500 expertise enhanced by AI to protect your business.
Battle-Tested Expertise
Leverage the same expertise that protected Fortune 500 companies against sophisticated cyber threats at Symantec's Attack Investigation Team.
- Advanced threat hunting methodologies
- Nation-state attack detection expertise
- Real-world incident response experience
AI-Powered Alert Triage
Our AI investigates every alert with the precision of a senior analyst, reducing 11,000 daily alerts to actionable intelligence.
- 95% reduction in false positives
- Automated forensic investigation
- 24/7 continuous monitoring
Enterprise Security on Your Terms
Get the capabilities of a full SOC team at a fraction of the cost of traditional MDR services or in-house teams.
- Save $300K+ vs. building an in-house team
- 75% less than traditional MDR services
- No long-term contracts required
See Your Potential Savings
Compare MalTrak to traditional security solutions
In-House SOC Team
$450K+/year
3 analysts + tools + training
Traditional MDR
$300K/year
Base service + endpoint coverage
MalTrak Solution
Contact Us
Full protection + AI capabilities
AI Investigate
Security Investigation Reimagined with AI
The first AI-native security platform built from the ground up to automate expert-level investigation techniques
 >
>
AI-Native Architecture
Built from the ground up with AI at its core - not a ChatGPT wrapper or add-on. Our AI models are trained on 17 years of real-world security investigations.
Expert-Level Analysis
Leverages our experience from Symantec's Attack Investigation Team, investigating world's most sophisticated attacks and nation-state threats.
Comprehensive Collection
Advanced volatile and non-volatile artifact collection enables thorough investigation of endpoints and servers for hidden threats.
Why AI Investigate is Different
True AI-native platform, not a traditional security tool with AI features added as an afterthought
Models built on real-world attack investigation data, not generic security patterns
Automated investigation workflows based on Fortune 500 security team practices
Advanced Capabilities
Deep learning models trained specifically on APT and targeted ransomware attack patterns
Continuous learning from new threats and attack techniques
Expert-level guidance for threat response and mitigation
Our Solutions
Comprehensive Security Coverage
From AI-powered investigation to specialized training, we provide end-to-end security solutions.
AI Investigate
Next-generation digital & memory forensics powered by state-of-the-art AI that models our expertise in investigation and insights in detection and response.
Continuous Threat Detection, Hunting & Exposure Management
Stop wasting time on fixes that don't impact risk. Quickly uncover all security exposures in your on-prem or cloud environment and zero-in on the ones that an attacker would chain together to form attack paths to critical assets.
Specialized Advanced Training
Expert-led training in malware analysis, reverse engineering, incident response, threat hunting, and red teaming. Includes a 3-month implementation & consultation plan to bridge theory and practice.
Your Digital Guardian
Protect Your Business Legacy
Let our AI safeguard what you've worked so hard to build
Protect What Matters Most to Your Business
Your team has worked tirelessly to build your business. Don't let sophisticated cyber threats take that away. Let our AI be your digital guardian, protecting your legacy 24/7.
Our Team
World-Class Security Expertise
Led by industry veterans with proven track records in cybersecurity

Amr Thabet
Founder & CEO
Amr Thabet is a distinguished security consultant and malware researcher with over 17 years of experience in cybersecurity. His career spans roles at Fortune 500 companies, including Symantec and Tenable, where he has established himself as a leading authority in malware analysis and advanced threat detection.
He is the author of "Mastering Malware Analysis," one of the highest-rated books in the field, published by Packt Publishing. This comprehensive guide has become a go-to resource for security professionals worldwide looking to develop their malware analysis skills.
As a key member of Symantec's Attack Investigation Team, Amr monitored sophisticated threat actors worldwide, including nation-state operators and hackers-for-hire. His work involved analyzing how elite hackers breach some of the world's most secure networks, including major technology companies, financial institutions, embassies, and healthcare organizations.
Amr has played a pivotal role in uncovering some of the most significant malware threats in modern history, including Stuxnet, Regin, and Contopee. His analysis of these sophisticated cyber weapons has provided crucial insights into how malware can be weaponized against critical infrastructure, most notably exemplified by Stuxnet's impact on Iran's nuclear program in 2010.
A respected voice in the global security community, Amr regularly speaks and conducts training at premier security conferences worldwide, including BlackHat, DEFCON, Hack In Paris, and VB Conference. His expertise has been recognized by major media outlets, including the Christian Science Monitor's coverage of his work on Stuxnet.
Today, Amr's mission is to combine his extensive expertise with state-of-the-art AI to protect organizations against sophisticated targeted attacks.

Grant Knoetze
Digital Forensics Expert
Grant Knoetze is a distinguished cybersecurity expert specializing in Digital Forensics and Incident Response (DFIR). His extensive experience includes training international cybersecurity professionals and U.S. law enforcement agencies in digital forensics techniques and methodologies.
With advanced expertise in Python, PowerShell, and system administration, Grant brings a comprehensive technical foundation to complex forensic investigations. His contributions to the field extend beyond practice to thought leadership, including publications in respected platforms like IT Pro Today.
As a frequent co-presenter with Amr Thabet at prestigious security events such as Hack in the Box, Grant continues to shape the future of digital forensics through his practical experience and innovative approaches to cybersecurity challenges.
Technology Edge
Enterprise-Grade Security Infrastructure
Powered by advanced AI and built on industry-leading security standards
Advanced AI Capabilities
Our AI engine leverages cutting-edge machine learning to:
- Automate forensic analysis
- Detect zero-day threats
- Predict attack patterns
Integration Ecosystem
Seamlessly integrate with your existing security stack:
- SIEM platforms
- EDR solutions
- Cloud platforms
Security Standards
Built on industry-leading security frameworks:
- MITRE ATT&CK Framework
- ISO 27001 compliance
- SOC 2 certified
Ready to Secure Your Business?
Schedule a consultation with our security experts and see how MalTrak can protect your organization.
Knowledge Base
Security Intelligence Center
Latest threat research, analysis reports, and security insights
Threat Analysis Reports

APT41's Fileless Attack: Abusing Microsoft Legitimate Applications For Security Mitigation
An in-depth analysis of APT41's latest attack methodology, utilizing fileless techniques and legitimate Microsoft applications to bypass security controls.

APT36: Uncovering South Asian Cyber Espionage Operations

Inside Cozy Bear's Arsenal: Advanced Persistence Techniques

APT41's Supply Chain Attacks: Following the Digital Breadcrumbs
On-Demand Webinars
The Only Step-by-Step Guide You Need to Combat APT & Targeted Ransomware Attacks Using Threat hunting
The top 4 reasons you are vulnerable to these attacks and how to implement threat hunting today to become more resilient against these attacks.
Latest from Our Blog
Don't Fall Behind
The Threat Landscape is Evolving
Is your security keeping up with sophisticated AI-powered attacks?
Every Minute Without AI Protection is a Vulnerability
While others are already leveraging AI to protect their networks, every delay in implementation leaves your organization exposed. Don't wait until after an incident to modernize your security.

Protecting businesses against targeted attacks through AI-powered security intelligence and expert-led services.
Inniscarra, Main Street, Rathcoole
Dublin, D24 E029, Ireland
support@maltrak.com
Resources
Company

Protecting businesses against targeted attacks through AI-powered security intelligence and expert-led services.
Inniscarra, Main Street, Rathcoole
Dublin, D24 E029, Ireland
support@maltrak.com
Resources
Company

©2024 MalTrak Limited - All Rights Reserved.
Inniscarra, Main Street, Rathcoole, Dublin, D24 EO29
AI Investigate
A Cost-Effective Approach To Detect, Respond To Targeted Ranosomware Attacks & Improve Your Security Posture
Our Partners & Clients




THE RELENTLESS THREAT
Malware has become the top threat leading to data breaches according to FireEye Cyber Trendscape Report 2020 which could cost up to €20 million in fines, or up to 4% of the annual worldwide turnover of the preceding financial year, whichever is greater.
Small & med-sized businesses are not far from the threat. 22% of small-med-sized businesses that experienced a ransomware attack ceased business operations immediately and 55% of them that lose data become unprofitable within 30 days. (Sources: HelpNetSecurity & Better Business Bureaus 2017)

Every security solution company is promising a silver-bullet. But a product or service is only as good as the people involved. MalTrak employees the foremost experts in the fields of malware/ransomware research and protection services.
We stand behind all our services with a real protection guarantee
Why MalTrak
Most businesses have some capacity to deal with security issues at some level. The problem is, attacks are getting more complex, more serious, more expensive, and more frequent. We shore up the operational process and technical gaps for every business to be able to operate more securely across all of Europe.
YOUR ENTERPRISE UPLIFT
Most businesses have some capacity to deal with security issues at some level. The problem is, attacks are getting more complex, more serious, more expensive, and more frequent. We shore up the operational process and technical gaps for every business to be able to operate more securely across all of Europe.

Audit & Analysis
We start by examining what measures are already in place, and where there are known issues, as well as where both newer and traditional attack vectors may hit.

Process Architecture
How you deal with your preparations, as well as any actual incidents, is critically important. We'll pull apart and rebuild your processes to harden your organisation.

On Premises Training
Not only do we perform the critical security tasks for you, we teach you IT teams how to improve their security capabilities too, keeping your organisation more secure.
ENTERPRISE SOLUTIONS
Network
Network security is a fundamental aspect of security for any organisation. We'll help you discover critical security threats so we can make the right adjustments to safeguard it against threats getting inside your walls.
Identity
Identity and Access Management (IAM) is how organisations ensure ONLY the right users have access the resources connected to your network. This reduces the potential for any threat actors to move across your networked assets, and also help improve productivity by reducing friction for legitimate requests. We'll establish and implement the right frameworks and policies to get the optimal outcomes from IAM implementations, all while reducing risk.
Infrastructure
Whether your business operates entirely on-premises, cloud-first, or a hybrid model, your IT ecosystem has innumerable connecting points that are often the vector for attacks. Poor patch and update management policies - if any - and suboptimal systems architecture leads to your business being insecure, ineffective, and inefficient when it comes to financial investment and other resources.
Endpoint
Endpoint protection has come a long way in the past decade, and for a good reason. Your users are typically the first targets in any threat actors attempts to compromise your security. While Security Awareness Training (SAT) should be mandatory, users can still get caught out by sophisticated phishing and social engineering campaigns. We provide better endpoint security so your people can do their best work safely and stay productive.
THE MALTRAK ADVANTAGE
How would your people respond to a REAL cyber attack? Not just your technology teams, but your financial, legal, operational, and leadership teams too? We build a comprehensive plan with you to test the responses your people have to perceived real-world cyber threats, and make sure you're prepared when the real time comes.
Much more than just pentesting or vulnerability assessments, we actually deploy "real" threat actors to pose as attackers that are trying to take down your company.Much like the movie trope of the ex-robbers hired to test new security systems at a bank, we test all the moving parts of your protection and response systems
OUR PROCESSES FOR YOUR BUSINESS
Threat Detection & Exposure Audit
We help discover existing threats and areas of potential exposure, and help break through your existing echo-chamber to see your risks objectively.
Our audit processes provide a high-level cyber evaluation of your company's IT environment, uncovering your organisation's threats, weaknesses, and vulnerabilities to better prepare, and to comply with critical standards like ISO 27001:2013 and other regulatory concerns
Continuous Threat Detection & Threat Hunting
Our team of experts not only uncover any existing compromises and threats to your business, but prepare you for the next round.
Every day, 350,000 new malware variants are discovered. Only 99.5 percent of them will be blocked by your current security procedures. That implies your security equipment are vulnerable to 1750 new malware assaults every day.
So, even if your current security measures are able to reject 99.5 percent of new malware every day, there are still over 1,750 malware threats that can sneak past your security controls and onto your network. Worse, studies suggest that most threat detection programmes in place in enterprises are unable to prevent 50% of new threats.
Red Team & Adversary Simulation
How would your people respond to a real cyber attack? Not just your technology teams, but your financial, legal, operational, and leadership teams too? We build a comprehensive plan with you to test the responses your people have to perceived real-world cyber threats, and make sure you're prepared when the real time comes.
Much more than just pentesting or vulnerability assessments, we actually deploy "real" threat actors to pose as attackers that are trying to take down your company. Much like the movie trope of the ex-robbers hired to test new security systems at a bank, we test all the moving parts of your protection and response systems.
WHAT OTHER STUDENTS SAY ABOUT OUR TRAINING?



Amr Thabet
Amr Thabet is a malware researcher and an incident handler with over 10 years of experience, he worked in some of the Fortune 500 companies including
Symantec, Tenable, and others.
He is the founder of MalTrak and the author of "Mastering Malware Analysis" published by Packt Publishing.
Amr is a speaker and a trainer at some of the top security conferences all around the world, including Blackhat, DEFCON, Hack In Paris and VB Conference. He was also featured in Christian Science Monitor for his work on Stuxnet.
His mission is to help security professionals all around the world to build their expertise in malware analysis, threat hunting, red teaming. and most importantly, protect their organization's infrastructure from targeted attacks, ransomware attacks, and APT attacks.

NOT YET READY YET?
You can check out our resources that will show you exactly the quality and support you can expect from our Master's Program and our Training programs, and see why MalTrak students are in such high demand
Watch Our On-Demand Webinars
The Only Step-by-Step Guide You Need to Combat APT & Targeted Ransomware Attacks Using Threat hunting
The top 4 reasons you are vulnerable to these attacks and how to implement threat hunting today to become more resilient against these attacks.
Equip Your Team With Necessary Tools
Expert-Written Cheat Sheets To Respond & Hunt For Targeted Attacks
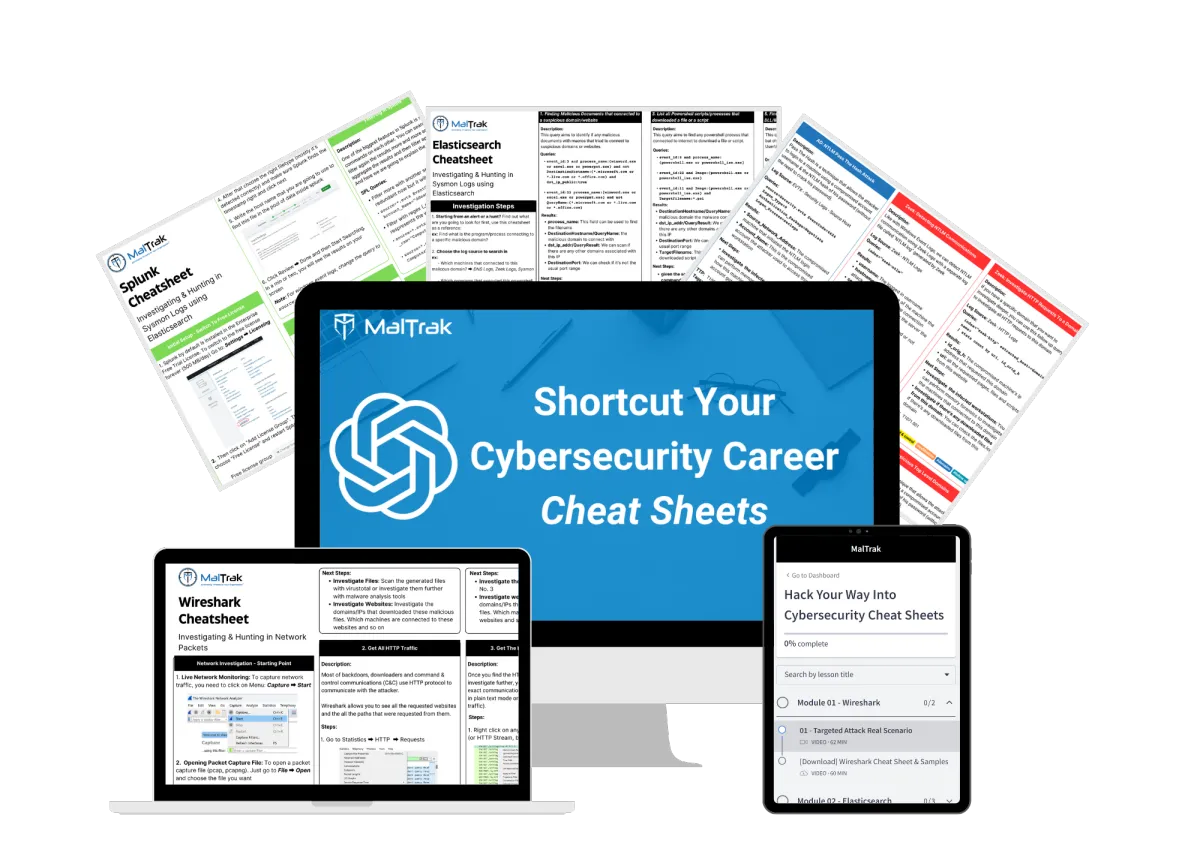
These are 3 expert-crafted copy-paste cheatsheets accompanied by a hands-on training to help you impersonate an expert in the field, analyze real cybersecurity attacks, and respond to targeted attacks and ransomware attacks
Get Our Book

WHAT ARE THE TRAINING PREREQUISITES?
All you need is:
➡️ Good IT Administration Background especially in Windows (Linux preferred)
➡️ Good Cybersecurity & Network protocols background
➡️Only in red team training: C++ Programming Background
WHAT HARDWARE/SOFTWARE IS REQUIRED?
Laptop with minimum 8GB RAM and 10-20 GB free hard disk space
IS THIS A LIVE TRAINING OR ON-DEMAND COURSE
It's a live 4-days training delivered either in person or virtually through Zoom
IS THERE A RECORDING? HOW LONG DO I HAVE ACCESS TO THE CONTENT?
In case of virtual event (through zoom), you will have access to the recordings for one year after the training
DO I GET A CERTIFICATION OF COMPLETION AFTER THE TRAINING?
Yes, you will.